Digital twin technology can strengthen cybersecurity strategies.
Image source:Getty Images/iStockphoto
Manar Alohaly
Senior Director of Advanced R&D and Innovation at Saudi Information Technology Company (SITE)
- The digital twin technology market is expected to continue growing rapidly.
- This technology is still primarily seen as a three-dimensional replica of physical assets.
- However, this view overlooks its potential in cybersecurity applications.
GartnerThe report states that the digital twin market is projected to grow from $35 billion in 2024 to $379 billion by 2034.Mordor IntelligenceSimilar growth forecasts have been made for the broader digital twin market, projecting it to expand from approximately $26 billion in 2024 to nearly $131 billion by 2029. While other predictions may vary slightly in their specific figures, they all consistently highlight the remarkable growth trend ahead.
This growth is primarily driven by the deep integration of the Internet of Things (IoT), artificial intelligence (AI), and cloud computing. As these enabling technologies continue to evolve, the potential of digital twins is steadily expanding. CEOs have already taken notice—according to a report, "70% of C-suite technology leaders at large enterprises are already exploring and investing in digital twin technology."
What is a digital twin?
Mentioning the digital twinMost people immediately think of 3D replicas of real-world objects when they hear the term "digital twin." But in reality, digital twins are far more than that.Digital TwinIt is a digital representation that can showcase physical objects from the real world,A system or process, andTwo-way interactions that can synchronize with their real-world counterparts. They are primarily categorized into the following types:Type:
- Component Twin: Sometimes referred to as a Part Twin, it represents the most granular level in a digital twin. As the name suggests, it focuses on modeling individual components of larger objects in the real world.
- Product Digital Twin: Essentially composed of multiple component twins combined to represent a complete product or device. This digital twin model can encompass the entire lifecycle of a product, from conceptual design all the way through full-scale production.
- Process twins are a digital representation of real-world processes, simulating the interactions and dynamics among the system's various components. Although still an emerging concept, they have already garnered significant attention within the industry.
- System Twin: is a comprehensive digital model that showcases how multiple product or process twins interact and operate as an integrated system.
1. Physical Security
Designing an effective security system for a physical environment requires careful consideration of numerous variables. Improper placement or poor positioning of security equipment—such as CCTV cameras—can create vulnerabilities. On the other hand, installing too many cameras and high-tech accessories in the system can lead to unnecessary, substantial expenses.
In this context, creating a digital twin of the physical environment can offer a range of benefits, from real-time monitoring to optimized resource allocation. It enables predictive analytics and scenario planning, helping businesses anticipate threats and develop proactive, effective defense strategies.
By optimizing security settings and configurations, digital twin solutions can help physical security projects achieve cost savings of 10% to 50%.
2. Digital Twin
As the digital landscape evolves with advancing technology, it’s becoming increasingly complex, presenting businesses with significant challenges in maintaining comprehensive network visibility, ensuring compliance verification, and identifying potential vulnerabilities. These challenges can lead to security breaches, heighten operational risks, and slow down response times to various requests. Fortunately, network digital twins offer a real-time, holistic replica of the network, enabling seamless validation and verification of configurations and security policies across all network components—empowering organizations to tackle these obstacles effectively.
A network digital twin is aTransformativeTechnology can reduce request response time by 20%.
3. A Digital Twin of the Security Operations Center (SOC) in the Information Technology (IT) and Operational Technology (OT) domains
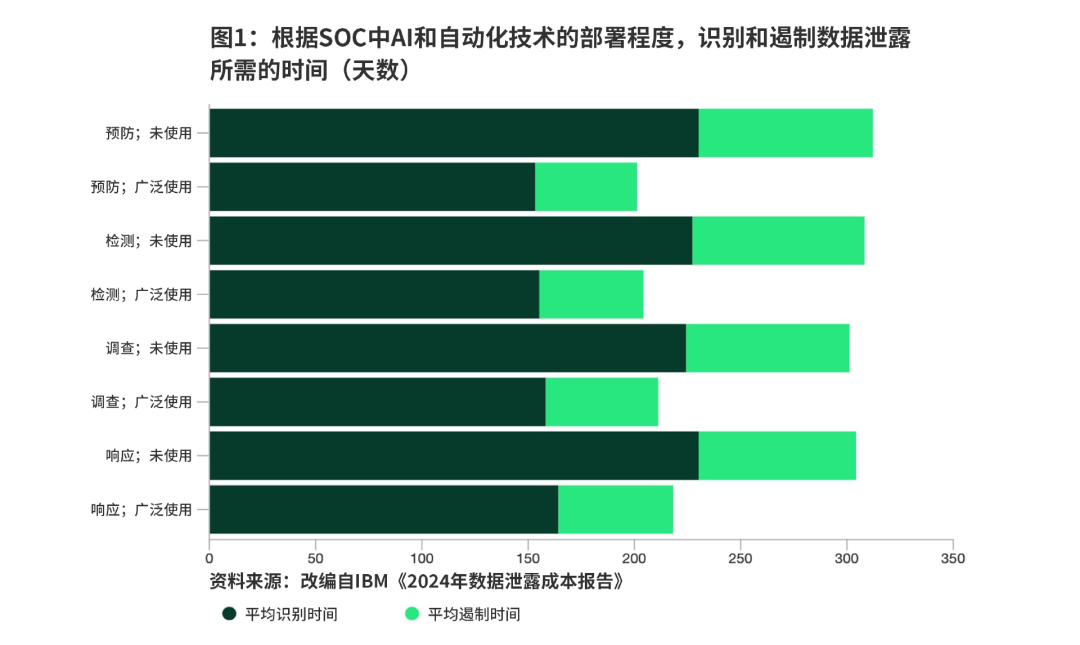
Cyber threats are becoming increasingly sophisticated,Traditional cybersecurity measures are gradually losing their effectiveness. IBM's"2024 Data Breach Cost Report"(The 2024 Cost of a Data Breach Report) reveals that 70% of organizations experience significant operational disruptions due to security breaches, with the average time to detect a breach standing at 199 days—and an additional 73 days required to fully contain the vulnerability.
Digital twin technology offers a powerful solution for cybersecurity threat modeling and incident response. By creating virtual replicas of an organization’s IT or OT infrastructure, security teams can simulate potential cyber threats in a controlled environment. For instance, digital twins can replicate the exact system to model the impact of ransomware attacks, helping businesses develop, test, and refine their incident response plans.
AI technology has already transformedThe vulnerability detection time at the Security Operations Center (SOC) was reduced by 33%, resulting in a 43% decrease in containment time.(See Figure 1), which illustrates the role of automation in incident response. Building on this, digital twin technology creates real-time virtual replicas, enabling the Security Operations Center (SOC) to simulate attacks and refine its defenses. This approach not only enhances visibility but also helps further strengthen cybersecurity—and could even potentially outperform purely AI-driven solutions.
Integrating Digital Twins into Cybersecurity Strategies
The digital twin market is experiencing explosive growth, with its value expanding from physical security optimization into cybersecurity areas such as network management and SOC operations.
Companies can conduct impact analyses to assess the benefits this technology could bring to their value chains, while also identifying potential risks. Pilot implementations can provide valuable insights, helping businesses evaluate effectiveness, refine related strategies, and ensure seamless integration of the new technology with existing systems before rolling it out across the board.

The above content solely represents the author's personal views.This article is translated from the World Economic Forum's Agenda blog; the Chinese version is for reference only.Feel free to share this in your WeChat Moments; please leave a comment at the end of the post or on our official account if you’d like to republish.
Translated by: Sun Qian | Edited by: Wan Ruxin
The World Economic Forum is an independent and neutral platform dedicated to bringing together diverse perspectives to discuss critical global, regional, and industry-specific issues.
Follow us on Weibo, WeChat Video Accounts, Douyin, and Xiaohongshu!
"World Economic Forum"